Several password plans, designed by your well-wishing system admins, instruct the user to have a complex code with Lowercase and uppercase letters, numbers, and several other alternatives involved. We are often dictated to keep a password that is hard to forget and harder to guess.
Additionally, the act of keeping the same or similar passwords for all accounts is strongly discouraged. But is all this complexity being maintained in the password selection area enough to protect the accounts or files from being hacked? Is it enough to secure our information? The answers can be both, ‘YES’ and ‘NO’.
Why ‘Yes’?
Complicated passwords make it harder for the hackers to make precise guesses. Hackers, if keep guessing randomly, will see the account locked after a limited number of wrong attempts to log in. The lockout detects intrusion and the administrators of the system are notified of suspicious actions. After that, it is all up to the admins. There are a number of programs which can crack simple dictionary-based passwords therefore having a password with complex combinations is always better.
Why ‘No’?
The intruder who has gained the admin access can bring to his use some very strong tools to crack the codes of the system. The hacker will be allowed to save the shadow files, the password, and other important information to a remote location. This procedure allows him to operate while sitting in the safety of his lab.
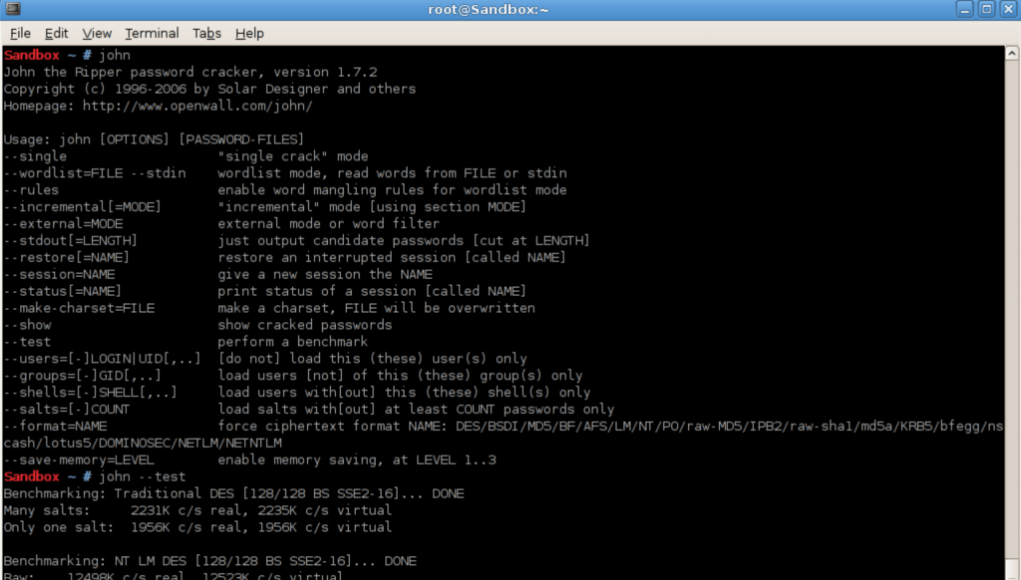
Hackers use various powerful programs to crack open accounts or password #files from systems, one of which is called ‘John the Ripper’. It is a free tool introduced by Openwall. System admins should use this program to carry out internal security audits, checking if their system can withstand such an attack. John the ripper password cracker is a simple-to-use program and is very small in size (1 MB).
Linux users wanting to start can download and install it from their Linux repository. From a certain source, they can compile and install John the Ripper. Windows users can simply download and install it from Openwall’s website.
John the Ripper is a command-line service, not requiring any administrative controls in order to work against a password hash file. However, in order to obtain these password hash files, some administrative privileges will be needed. Firstly, you should check how efficiently John can work on your system by running it in test mode, before you start trying to crack passwords. The report obtained will tell you how many combinations/sec (c/s) John can run while operating on your system for each password hash encryption type subject.
On Linux systems using shadow passwords, the following command can be issued to produce a password #file from the password and shadow files of your system.
“$ sudo john unshadow /etc/passwd /etc/shadow > passfile.txt”
Once the file is created, the crack attempts start. The simple dictionary based passwords take much less time, even as short as minute to be cracked open. System admins must educate the users on how to make the strongest passwords for their own security.
A good password,
- Consists of at least 10 characters.
- Contains lower and upper case letters.
- Contains numbers and special characters.
- Is random.
John the ripper may eventually crack any password, however having a complicated one will give the user more time to respond to the warning messages and change the login info.