In recent times McIntyre has given information to the famous DNC hacking back in 2016 and his discoveries have been especially intriguing.
Before acquainting you with the news of malware on DNC server, let us tell you about some background to this news:
Late April 2016
At the end of April 2016, the Democratic National Convention outsourced a cyber-security firm with concerns of a suspected breach.
Early May 2016
The cyber security firm visits the DNC server system and reveals the DNC malware hack. The cybersecurity firm asks DNC to install their product known as FALCON to stay unharmed. Consequently, DNC starts paying the standard subscription fee to the cyber security firm.
 Late May 2016
Late May 2016
The data of emails of mid-May is breached and leaked to WikiLeaks.
June 2016
WikiLeaks indicates that they possess data related to emails.
In the next 48 hours of the declaration (on June 14, 2016), an article showed up in the Washington Post, covering a story from CrowdStrike (cyber security firm). In the article, they claim to have recently been taking a shot at wiping out the remainder of the programmers from the DNC’s system and indirectly admitted to the failure of their software in fulfilling its promised capabilities.
Now coming to the present year 2017, earlier this month, a person pointed out on Twitter about the mismatch of the date of malware with the compilation date.
@with_integrity – do you know how to interpret the "First Seen In the Wild"? date in the virustotal database? Does it relate to the source code of the malware? Or maybe a malware package the file belongs to? Is the Compilation Timestamp credible?https://t.co/rvxfaTAmUE
— c.t.alhambra (@ct_alham) December 9, 2017
This issue sparked a new dilemma of whether the malware was made at some earlier date but somehow its compile date was postdated.
But the big question remains:
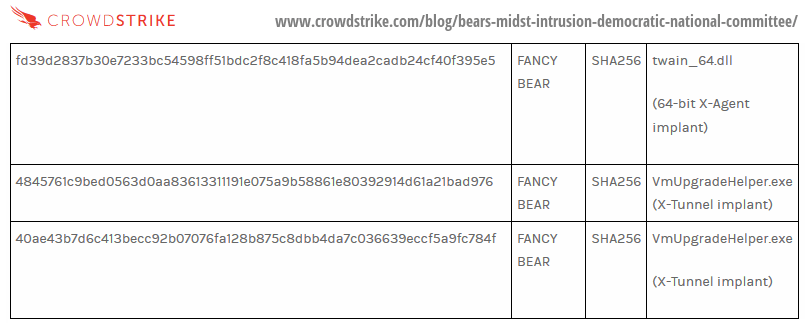
Did CrowdStrike plant some (or all) of the APT-28 malware?
This answer was found in the information in IP addresses found in the malware information:
Thomas Rid pointed out:
“Remarkably the same C2 IP actually is hardcoded in the DNC and BUNDESTAG APT28 samples.”
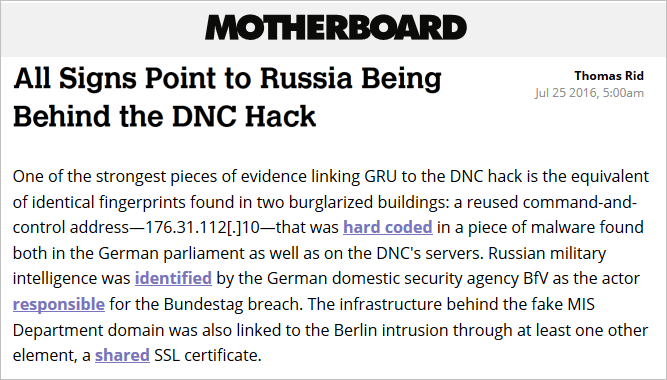 This proof was further confirmed by analysis of the DNC malware hack at Invincea.
This proof was further confirmed by analysis of the DNC malware hack at Invincea.
The way that two out of three of the Fancy Bear malware tests recognized were aggregated on dates inside the clear five day time frame CrowdStrike were obviously at the DNC appears to be fantastically far-fetched to have happened by chance. Moreover, the fact that each of the three malware tests were aggregated inside ten days either side of their visit – influences it to clear exactly how flawed the Fancy Bear malware revelations were.
Last but not the least, the malware was evidently utilizing surely understood and long-excess hardcoded IP addresses just appears to be peculiar, isn’t that right?
Stay tuned to our news for further updates on this news of DNC malware hack.



