
The router is the first point of entry for hackers who try to access all your internet-connected devices.Unfortunatelly, it’s easy to surpass the protection offered by many of the top Wi-Fi routers. That’s why it’s important to take some time and setup your router properly.
There are a couple of basic settings that are very easy and most of you know them, so we’ll present them very briefly before we get to real important settings:
- If possible, change the default administrator username, password and IP address
- Change the name of your wireless network(SSID) so your devices don’t accept connections to similarly named networks and also you avoid telling the hackers what model of router you are using(e.g. “D-Link, TP-Link”)
- Set the wireless security mode to WPA2 and choose a long and secure password for it
As you may think, beside taking in consideration these basics, there are a couple more advanced settings to make before sleeping totally relaxed at night, especially taking into consideration the latest security and spying issues.
Install DD-WRT or Tomato if it’s supported by your router
Open-source router firmware DD-WRTand Tomato add a plethora of features to your router and it’s also more secure than the stock firmware delivered with the router. These custom firmwares are patches to solve the vulnerabilities found in many routers, such as the well knownproblemregarding WPS (Wi-Fi Protected Setup). They get updates more frequently, have more security options (advanced logging or encrypting DNS with DNSCrypt), and give you more control over different hardware parameters. Security expert Brian Krebs says:
“Most stock router firmware is fairly clunky and barebones, or else includes undocumented “features” or limitations.Normally when it comes to upgrading router firmware, I tend to steer people away from the manufacturer’s firmware toward alternative, open source alternatives, such as DD-WRT or Tomato. I have long relied on DD-WRT because it with comes with all the bells, whistles and options you could ever want in a router firmware, but it generally keeps those features turned off by default unless you switch them on.”
DD-WRT is dedicated more towards the professional being packed with more settings, while Tomato is more user friendly which makes it accessible for more people. You can check the supported devices page for DD-WRT and Tomato to see if they’re compatible to your router.
Periodically update your firmware
It’s important to keep your router’s firmware updated to the latest version, no matter what firmware you use, stock or custom. Bugs and vulnerabilities are frequently discovered and addressed through new revisions, like the Linksys bug that gave remote users access to the administration console without having to log in.
The steps required to update the firmware varies by one manufacturer to the other, but usually you can check from updates and flash them through the router’s web interface. In some cases it may be required for the user to check and download the firmware manually from the manufacturer’s website.
Turn off remote administration
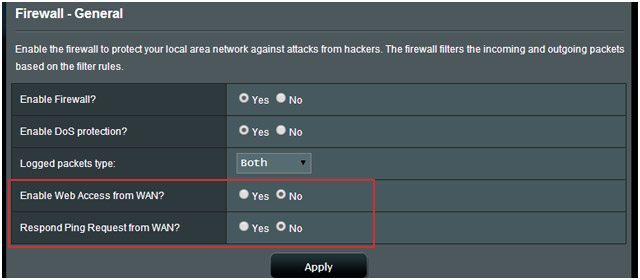
Although this feature is turned off by default on many routers, you may want to check this before reading this article further. You can find this feature under Advanced or Administrative section in the web interface, under the names Web Access, Remote Management or Remote Administration. If it’s enabled it will permit the access to your router’s control panel from outside your network, which makes the job of a hacker much more easier.
Disable UPnP
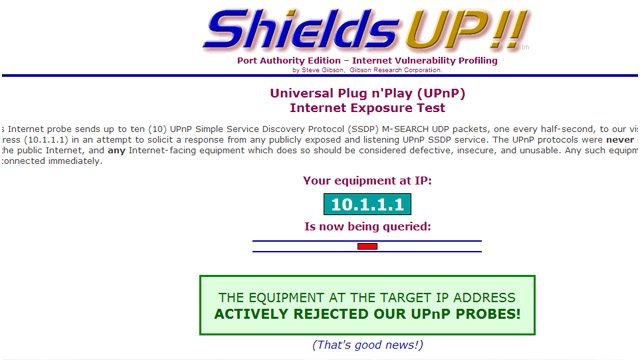
The purpose ofUniversal Plug and Play (UPnP) is to make the router discover the devices attached to the network. The problem is that there are serious bugs and security holes, fueled by the poor implementation of this protocol. UPnP doesn’t rely on authentication, that’s why hackers can use it easily to install malicious apps that can reroute traffic to different IP addresses outside of the LAN.
You can use GRC’s UPnP test to find out if your devices and data are insecure and exposed to the internet. (to run the actual testclick the red ribbon on the top right of the webpage).
To turn it off, find the UPnP setting and disable it in the Administration or Advanced section of the router’s management console. If available, you can turn off also the “Allow user to configure UPnP” option. Disabling UPnP only affects things outside your local network, meaning that other features using this protocol will still work in your own LAN (e.g. video streaming). It’s possible that you have to setup port forwarding in order to keep programs like uTorrent or BitTorrent functioning properly.
Other security mythsthat may not worth the trouble
SSID Hiding
Hiding your router’s SSID may sound like a good idea in the beginning, but it’sa chance that it will actually decrease your security. Wi-Fi security expert Joshua Wright explainsfor Tech Republic:
“Imagine you are a government base and you don’t tell your agents where you are located. They have to walk around and keep asking “Are you the government base?” to everyone the meet. Eventually, some wily hacker or bad guy will say “Heck YEAH I’m your base, come on in and share your secrets with me.” This is essentially what happens with SSID cloaking, where you have to ask every AP you meet if their desired SSID is available, allowing an attacker to impersonate your SSID at the airport, coffee shop, in the airplane, etc. In short, don’t cloak your SSID, but don’t make your SSID something like “sexyhackertargethere” either.”
While SSID hidding may be good for avoiding the neighbors that want to use your Wi-Fi network for free, it’s not keeping the hackers away, it may really increase their attention towards you.
MAC Filtering
MAC filtering can limit network access only to the devices you allow and can provide added security against the average Joe, but MAC addresses are easy to spoof. Stack Exchange user sysadmin1138 concluded:
“For someone who wants your network specifically, encryption (most especially un-broken encryption) will provide vastly better security. MAC spoofing is trivial in most adapters these days, and after you’ve cracked the network to the point you can monitor in-flight packets you can get a list of valid MAC addresses. SSID is trivial at that point as well. Due to the automated nature of the toolsets available, MAC filtering and SSID hiding aren’t really worth the effort any more.”
Turning on MAC filtering it’s not a bad ideea but in the end it doesn’t worth the hassle as it gets very difficult when you get a new device or a friend comes to visit.
Static IP Addresses
One other setting you may think of changing is turning off DHCP (Dynamic Host Configuration Protocol) and assign static IP addresses to all your devices. The advantage is that unknown devices will not be given any address, but also using static IPs also have its downsides, as this discussion on Stack Exchange points out.
The conclusion is that we cannot establish which one is better for security because static IPs is vulnerable to spoofing attack, while DHCP devices can be attacked by rogue servers.
SOURCE: LIFE HACKER

