The integrity that the hacking field has achieved in the recent past is phenomenal. Both sides of hacking: unethical or ethical, have progressed so rapidly that even the most secure authorities in the world are not safe at any point.
A proof of this insecurity is provided by the recent discovery and revealing of the wireless router hacking tool formulated ingeniously by the Central Intelligence Agency (CIA). This confidential information was leaked by the famous WikiLeaks. WikiLeaks made this discovery public in its famous series known as Vault 7 leak. (Vault 7 leak is a series of hacking discoveries made by WikiLeaks regarding CIA)
This news shocked everyone because the mind boggling fact came up that CIA has the ability to break into iPhones, Android phones, smart TVs, and Microsoft, Mac and Linux operating systems. Amongst these revelations is the “Cherry Blossom” which is believed to be part of a bigger project i.e. “Cherry Bomb”. The main objective behind this project is to exploit the vulnerabilities in smart devices to have open access to their internet activity.

According to the revelation, “Cherry Blossom”, the wireless hacking tool, was formulated by the Stanford Research Institute for the CIA. The formulators have given Cherry Blossom the face of a firmware which is remotely accessible. It has the ability to capture security lapses in the wireless routers of countless devices to have illegal access. This enables them to then install Cherry Blossom’s firmware into the device to have permanent and unauthorized access to any device. All of this activity is controlled from the CherryTree, a remote CIA command and control centre.
There are also leaked reports mentioning the installation of a software known as “Flytrap” which is particularly used to remotely send internet activity. This software’s installation is enabled through the Cherry Blossom’s firmware.
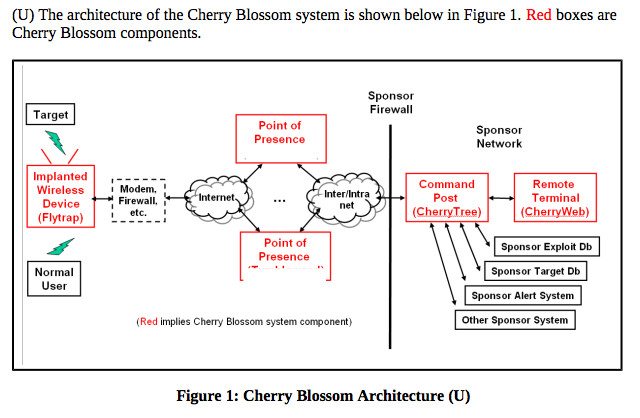
The fact that leaves jaws wide open is that all of this hacking process requires absolutely no physical access to the target device. Now what is the range of actions that this wireless router hacking tool can actually perform are: interception and collection of email addresses, VOIP numbers, and MAC addresses. Moreover, channelling users to malicious websites and even inserting exploitations to further harm the devices is what this “ingenious” wireless router hacking tool can actually do. Thus it is clear now that hacking is being used by the most integrated intelligence agencies of the world to exploit any vulnerabilities.



