Tor project advised for calm after research shows that 81% of users can be identified using NetFlow technology designed by Cisco.
The Netflow technology was launched by Cisco to its routers to employ the instrument for collecting IP network traffic while it enters and exits interface. Data provided by Netflow will allow a network administrator to qualify network traffic that are managed by router and recognize the congestion cause. This protocol is standard and running today by default in most hardware of other network device manufacturers.
According to the research group led by Professor Sambudah Chakavarty of Indraprastha Institute of Information Technology in Dehli University, influential attackers like nation-state hackers can identify Tor clients identity by way of false-positive rate of 6.4%, whereas autonomous system can reveal 39% of users.
An article from “On the Effectiveness of Traffic Analysis against Anonymity Networks Using Flow Records” describes how these hackers are resourceful to mount traffic analysis in observing similar traffic to a various points to the network while linking together other unrelated network connections.
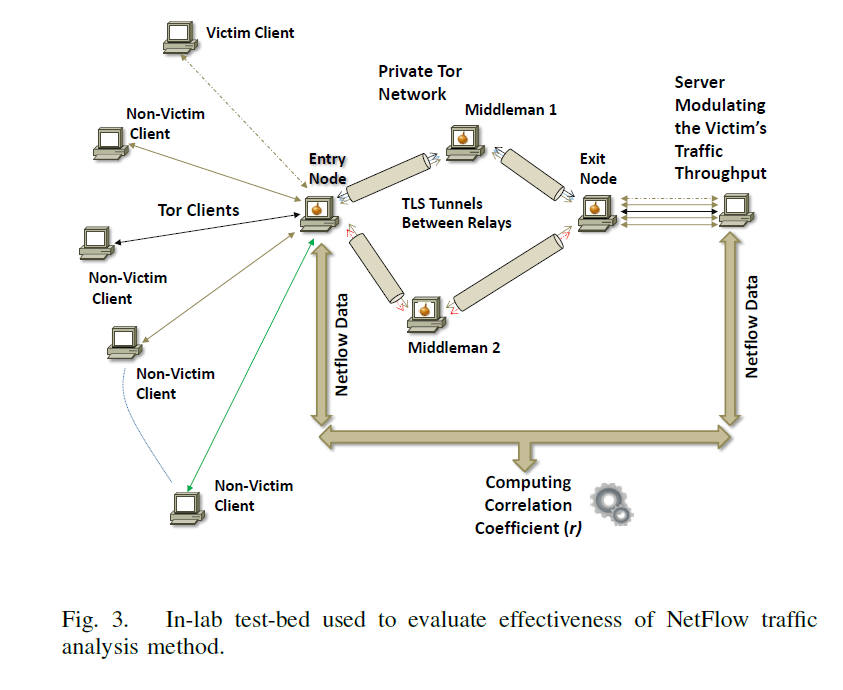
Sambudah Chakavarty’s group research runs on high performance research server in Dehli University worked as part due to the low-latency design of Tor. This team of five tested the technique to a public Tor relay to hundreds of users.
The research uses technique that injects a reiterating traffic pattern in the TPC connection that is associated with the exit node and compares them to the following aberrations in the network timing having the traffic flow records that are generated by Netflow to individuate the so called client “victim”.
In the laboratory, a condition success rate of the traffic analysis attack is 100%, while network noise or variations reduced efficiency of 81% within a live environment of Tor.
Chackravarty states that “It is not even essential to be a global adversary to launch such traffic analysis attacks.” The powerful but non-global adversary can use traffic analysis method for determining the diverse relays participating Tor circuit and openly monitor traffic entertaining the node of entry of the “victim” connection.
After the publication of the research, Tor admins told their users there is no reason to fear of identifying their identities. The discussion of the false positive is the key to the new paper. Sambuddoh’s paper mentioned a false-positive rate of 6%.
Roger Dingledine, the Tor Project Leader said in the blog post that “It’s easy to see how it scale this ‘base rate fallacy’ problem could make the attack effectively useless”.
Dangledine also emphasize whether the attack could be completed, all has to do with “how much of the internet the adversary is able to measure or control.”
To add more, Dangledine said that “it’s great to see more research on traffic confirmation attacks, but traffic confirmation attacks are not a new area so don’t freak out without actually reading the papers, and this particular one, while kind of neat, doesn’t supersede all the previous papers.”