Everywhere around us, we are covered with technologies and Signal Lights on roads also operated through the digital network and it is revealed and proved that Hacking Traffic lights is not a hard hack and even a college student able to hack the Traffic Lights.
According to the researchers at the University of Michigan claimed to hacked the traffic light signals in real life practically, Red Lights could be hacked easily through anyone by using a laptop and the right kind of ratio.
You already seen, how crazy is hacking red lights in the movies like: Die Hard and The Italian Job, and sometimes it also boost hackers to do as in the movie.
In a paper online, Researchers revealed a series of major security flaws in traffic light systems that allows an attacker to seize control of the traffic lights signals. At least 100 traffic signals in an unnamed Michigan city from a single point of access.
The vulnerabilities we discover in the infrastructure are not a fault of any one device or design choice, but rather show a systemic lack of security consciousness, paper reads.
What are the Loop Holes inside the Traffic Light Signals:
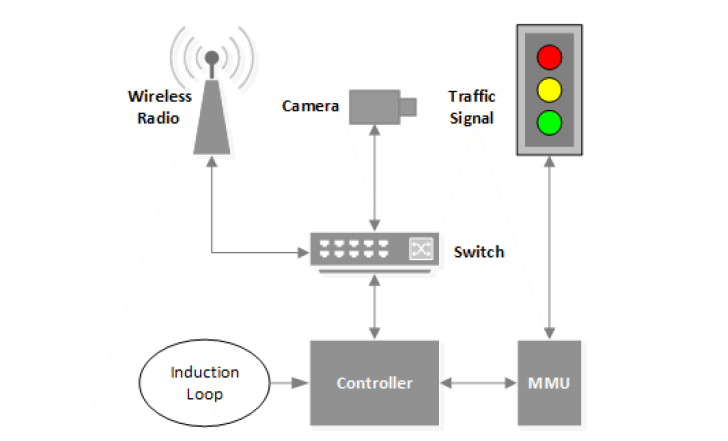
- unencrypted radio signals
- the use of factory-default usernames and passwords
- a debugging port that is easy to attack
Above are the Loop holes in the traffic signals systems that are still being used by the system for money saving, as this is a low budget traffic system. Physical traffic networking need more money to spend upon the systems.
‟Our attacks show that an adversary can control traffic infrastructure to cause disruption, degrade safety, or gain an unfair advantage,” the paper explained.
“The safety critical nature of traffic infrastructure requires that it be secure against computer-based attacks, but this is not always the case,” the team said. “We investigate a networked traffic signal system currently deployed in the United States and discover a number of security flaws that exist due to systemic failures by the designers. We leveraged these flaws to create attacks which gain control of the system, and we successfully demonstrate them on the deployment.”
To learn more about the Radio Signals Go Here
To learn more about the Debugging port Go Here
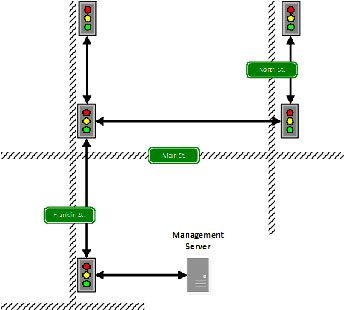
Example traffic signal network: