Gmail is the Mail service provider which is actually being used by every second or third internet user and this is the key for our other social accounts those connected with gmail like like Facebook, twitter and more are there, you better know than me :)
So, the point is have you ever seen all of the gmail addresses in the world or how will you react when you have access to all of the email addresses in the world related to GMAIL.
I will feel lucky because i want a bounty for this, same is done by a researcher of Israel named “Oren Hafif” who was able to find a vulnerability in Gmail systems to extract all of the email addresses from its database including internal email addresses.
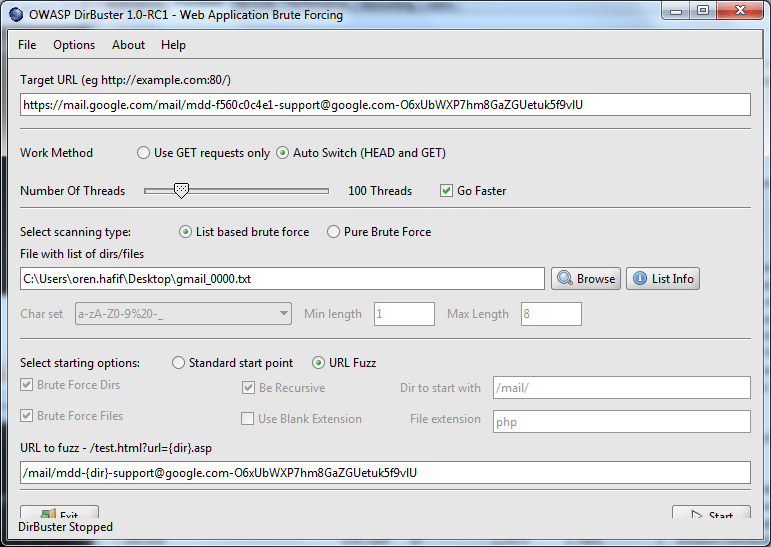
Oren found a bug in the Gmail delegation system, which is used to authenticate any other person to use the same account you using.
The Loop hole was actually in the URL sent by Google Systems to authenticate other email address to access account:
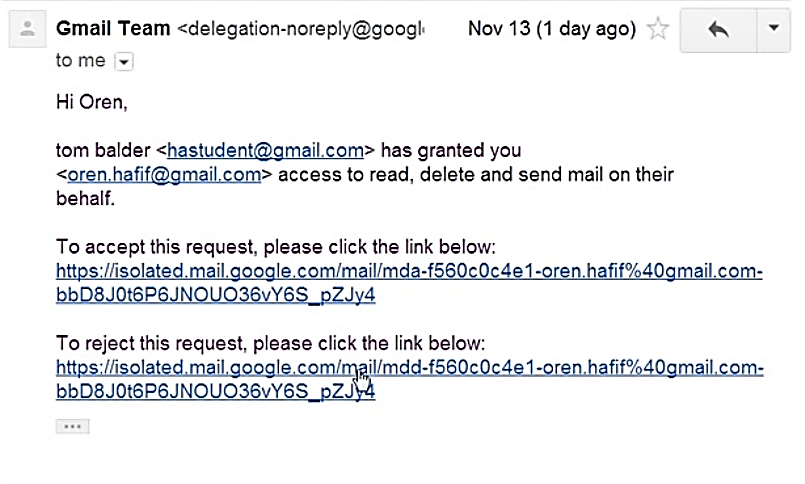
As you can see above, there are two URLs one for accept the invitation and second for Rejection.
Oren smartly described the URL:
Let’s take a closer look at the request URL
- https://mail.google.com/mail/mdd-f560c0c4e1-oren.hafif%40gmail.com-bbD8J0t6P6JNOUO36vY6S_pZJy4
- The first part “https://mail.google.com/mail/”, is just the normal mapping to the Gmail application.
- The second “/mdd” is the mapping for the mail delegation deny servlet.
- What does “f560c0c4e1” stand for? It looks like a token. There is some hope here, as this one is so short and it’s hexadecimal
- My email address – probably not relevant.
- What does “bbD8J0t6P6JNOUO36vY6S_pZJy4” stand for? It looks like an encoded blob. This is normally a BAD sign as Google loves to HMAC request URLs and that could be a giant “pain in the scans”.
He used the URL to FUZZ “/mail/mdd-{dir}[email protected],” and the Dictionary hold all 10-character long combinations of such an HEX-string.
After that, he used various tactics to by pass google server because he was requesting too many requests form Google that is unauthorized and google block us for that, for a complete demonstration you can see the video below or you can follow his blog HERE to see how he explored the jackpot of email addresses.
:)
In the meantime, this vulnerability has been fixed and Google rewarded Oren with $500.